Anderson Cooper’s Guide To AWS IoT Tunnel: Unlocking Secure Device Communication
Hey there! AWS IoT Tunnel is like a digital Swiss Army knife for IoT device management. It gives you a secure and efficient way to connect your IoT devices with external applications, even if they're hiding behind firewalls or NATs. As the IoT world expands across industries, making sure our devices are safe and reliable has never been more important. This guide is all about AWS IoT Tunnel—what it does, why it matters, and how you can put it to work for you.
Let’s break it down. AWS IoT Tunnel lets you talk to IoT devices that are tucked away in restricted networks without leaving any doors wide open. Think of it as a secure hotline between your devices and the outside world. Whether you're dealing with industrial machinery, smart home gadgets, or healthcare equipment, AWS IoT Tunnel keeps communication smooth, safe, and seamless.
In this deep dive, we're going to explore every nook and cranny of AWS IoT Tunnel. From its technical nuts and bolts to real-world examples, we’ll show you exactly how it works and how you can use it to level up your IoT infrastructure. By the time we're done, you'll be ready to rock with AWS IoT Tunnel like a pro.
Read also:Understanding The Complex World Of Antonia Mackenzies Digital Controversy
Table of Contents
- Introduction to AWS IoT Tunnel
- Why Use AWS IoT Tunnel?
- AWS IoT Tunnel Architecture
- Setting Up AWS IoT Tunnel
- Real-World AWS IoT Tunnel Example
- Security Features of AWS IoT Tunnel
- Common Use Cases
- Troubleshooting AWS IoT Tunnel
- Best Practices
- Conclusion
Welcome to AWS IoT Tunnel: Your Secure Connection Hub
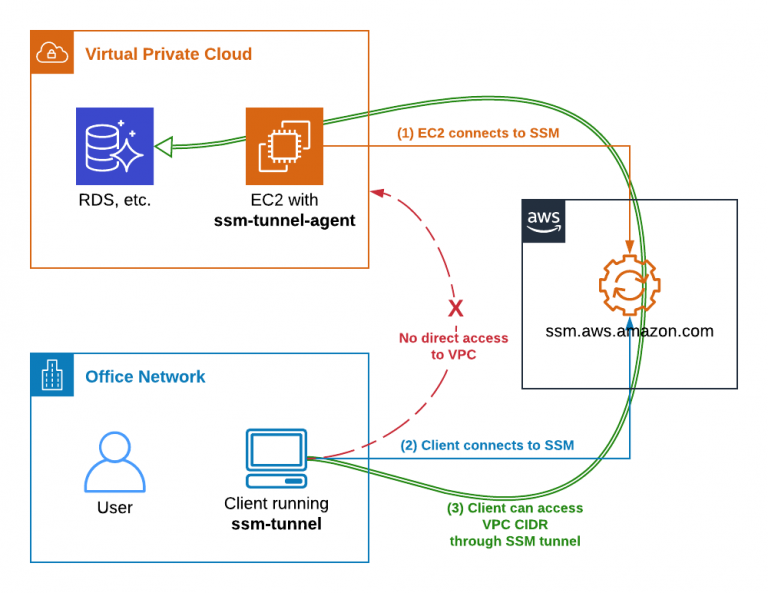
Alright, let's get started. AWS IoT Tunnel is basically a service that makes secure communication between IoT devices and external apps possible. It sets up a secure tunnel to devices that are locked behind firewalls or NATs, no need to leave ports wide open. This is a game-changer for managing devices in restricted environments.
The way it works is simple but genius. The tunneling process ensures only people with the right credentials can access your devices, keeping everything locked down tight while still being easy to use. AWS IoT Tunnel is part of the larger AWS IoT family, which includes heavy hitters like AWS IoT Core, AWS IoT Device Management, and AWS IoT Analytics.
Key Features That Make AWS IoT Tunnel Shine
- Encrypted tunnels for secure communication—no one can eavesdrop.
- No need to keep ports open on your devices—less risk, more peace of mind.
- Supports both TCP and UDP protocols, so it plays well with others.
- Works hand-in-hand with AWS IoT Core for seamless device management.
Why Should You Care About AWS IoT Tunnel?
Here’s the deal: AWS IoT Tunnel isn’t just another tool in the toolbox. It’s a game-changer for IoT device management. Let me tell you why.
First off, it beefs up your security game by making sure your devices aren’t exposed to the wild west of the internet through open ports. Instead, it uses a secure tunneling system that only lets authorized users in. This is huge when you're dealing with sensitive data or trying to keep unauthorized folks out.
Second, it makes managing IoT devices a breeze. You can connect to devices that are locked away in restricted networks without jumping through hoops or messing with complicated network settings. If you're running a business with tons of IoT devices, this is a dream come true. It’s like having a personal valet for all your IoT connections.
How AWS IoT Tunnel Works Under the Hood
The architecture of AWS IoT Tunnel is designed to be both secure and efficient. It’s like a well-oiled machine with different parts working together seamlessly. Here’s how it breaks down:
Read also:Aurora Belova Beyond The Buzz
- AWS IoT Core: This is the brains of the operation. It acts as the central hub where all device communication happens.
- Tunnel Manager: Think of this as the traffic cop. It handles the creation and termination of tunnels, making sure everything runs smoothly.
- Tunnel Proxy: This is the middleman that facilitates communication between the device and the application. It makes sure all the data flying back and forth is encrypted and secure.
When you set up a tunnel, the device and application chat through the tunnel proxy. This setup ensures smooth communication while keeping everything super secure. It’s like having a private line that no one else can tap into.
Getting AWS IoT Tunnel Up and Running
Setting up AWS IoT Tunnel might sound intimidating, but it’s actually pretty straightforward. There are a few steps to follow, and before you know it, you’ll have your secure tunnel up and running.
Step 1: Configure AWS IoT Core
Before diving into AWS IoT Tunnel, you’ll need to get AWS IoT Core ready. This involves creating a "thing" (which is just AWS-speak for a device), setting up policies, and configuring certificates for device authentication. Think of it as setting the stage for the main event.
Step 2: Create a Tunnel
Once AWS IoT Core is all set, it’s time to create your tunnel. You can do this using the AWS CLI or the AWS Management Console. When creating the tunnel, you’ll need to specify which device you’re targeting and set some parameters. It’s like picking a destination and planning your route.
Step 3: Establish a Connection
After the tunnel is created, it’s time to connect the device and application. This involves configuring the device to link up with the tunnel proxy and ensuring the application can communicate with the device through the tunnel. It’s the final step in making sure everything is talking to each other the way it should.
A Real-Life Example of AWS IoT Tunnel in Action
Let’s paint a picture. Imagine a manufacturing plant where IoT sensors are keeping an eye on equipment performance. These sensors are safely tucked behind a firewall, making it tricky to access them from afar.
Enter AWS IoT Tunnel. With it, the plant can create a secure connection to those sensors without leaving any ports open. This means engineers can remotely monitor and troubleshoot equipment, saving time and reducing downtime. It’s like giving the maintenance crew superpowers to keep things running smoothly.
Steps to Implement AWS IoT Tunnel in a Manufacturing Environment
- Install AWS IoT Core on the plant’s network—this sets the foundation.
- Create a tunnel for each sensor that needs remote access—think of it as building private roads for each device.
- Configure the sensors to connect to the tunnel proxy—this is where the magic happens.
- Grant engineers access to the tunnel through the AWS Management Console—now they’re ready to roll.
AWS IoT Tunnel’s Security Armor
AWS IoT Tunnel doesn’t mess around when it comes to security. It’s packed with features to make sure your device communication is locked down tight. Here’s what you get:
- End-to-End Encryption: All data moving through the tunnel is encrypted, so prying eyes can’t see what’s going on.
- Authentication and Authorization: Only authorized users can access the tunnel, keeping unauthorized folks out.
- Regular Security Updates: AWS keeps things patched and updated to address any vulnerabilities that might pop up.
These security features make AWS IoT Tunnel a trusted choice for businesses that need top-notch security for their IoT devices. It’s like having a digital fortress around your most important tech.
Where AWS IoT Tunnel Fits in the Real World
AWS IoT Tunnel isn’t just for one industry—it’s got applications across the board. Here are a few examples:
Remote Device Management
In situations where devices are out in the middle of nowhere or in restricted areas, AWS IoT Tunnel makes managing them a cinch. This is a big deal for industries like oil and gas, where equipment is often in remote locations. It’s like having a remote control for all your gear, no matter where it is.
Healthcare Device Monitoring
In the healthcare world, AWS IoT Tunnel can help monitor medical devices from afar. This ensures patients get the care they need quickly and that medical staff can respond to emergencies without missing a beat. It’s like having a virtual nurse keeping an eye on things.
Home Automation
For smart home systems, AWS IoT Tunnel provides a secure way to connect your devices to external apps. This lets homeowners control their gadgets from anywhere while keeping everything locked down. It’s like having a personal assistant for your home that’s always on the job.
Troubleshooting AWS IoT Tunnel: What to Do When Things Go Wrong
Even the best tools can have hiccups. If you run into issues with AWS IoT Tunnel, here are some steps to help you troubleshoot:
- Verify Device Certificates and Policies: Double-check that everything is set up correctly on the device side.
- Check Network Configurations and Firewall Settings: Make sure your network isn’t blocking the tunnel.
- Review Logs for Error Messages: Logs can be your best friend when trying to figure out what’s going on.
By following these steps, you can quickly identify and fix any problems, keeping your IoT infrastructure humming along.
Best Practices for AWS IoT Tunnel Success
Want to get the most out of AWS IoT Tunnel? Here are some tips to keep in mind:
- Regularly Update Device Firmware and Software: Keeping everything up to date helps prevent issues down the road.
- Monitor Tunnel Activity and Usage: Keep an eye on what’s happening with your tunnels to spot any potential problems early.
- Implement Strong Authentication and Authorization Mechanisms: The stronger your security, the safer your devices will be.
By following these best practices, you’ll be able to maximize the benefits of AWS IoT Tunnel and keep your IoT devices running smoothly and securely.
Final Thoughts on AWS IoT Tunnel
AWS IoT Tunnel is more than just a tool—it’s a powerhouse for secure IoT device communication. It gives you a dependable and efficient way to connect devices with applications, even in the trickiest environments. By following the steps in this guide, you’ll be able to set up AWS IoT Tunnel and take your IoT infrastructure to the next level.
We’d love to hear your thoughts and experiences with AWS IoT Tunnel in the comments below. And don’t forget to check out other articles on our site for even more insights into IoT and cloud computing. Together, let’s build a future that’s more connected and secure than ever before!
References:
Article Recommendations